The Implications of LinkedIn Automagically Knowing My Work Email Address

Hands up, how many of you were aware that LinkedIn had the capacity to automatically add a secondary or work email to your personal account without your knowledge? I certainly wasn't! A quick Internet search reveals I wasn't alone in questioning this wizardry.
My first reaction when this was brought to my attention was to assume well, LinkedIn has access to much of my personal information including where I work, and subsequently who my colleagues are. Therefore it wouldn't be a massive leap of faith to suggest that LinkedIn probably knows the email pattern associated with my employers domain (for example, [f.lastname, first.lastname, first.l, technology, quality_assurance]@example.com). All that would be required to deduce this pattern is at least one of my colleagues registering their work email as their primary or secondary email address within their LinkedIn settings page.
It turns out, to my best knowledge, LinkedIn is not doing this. And if privacy is near the top of its agenda, nor should it be doing this. That didn't stop security researchers using this method to identify Mark Cuban's email address through LinkedIn's email invitation system though!
So how, then, does LinkedIn know my other email addresses?
What's the secret sauce?
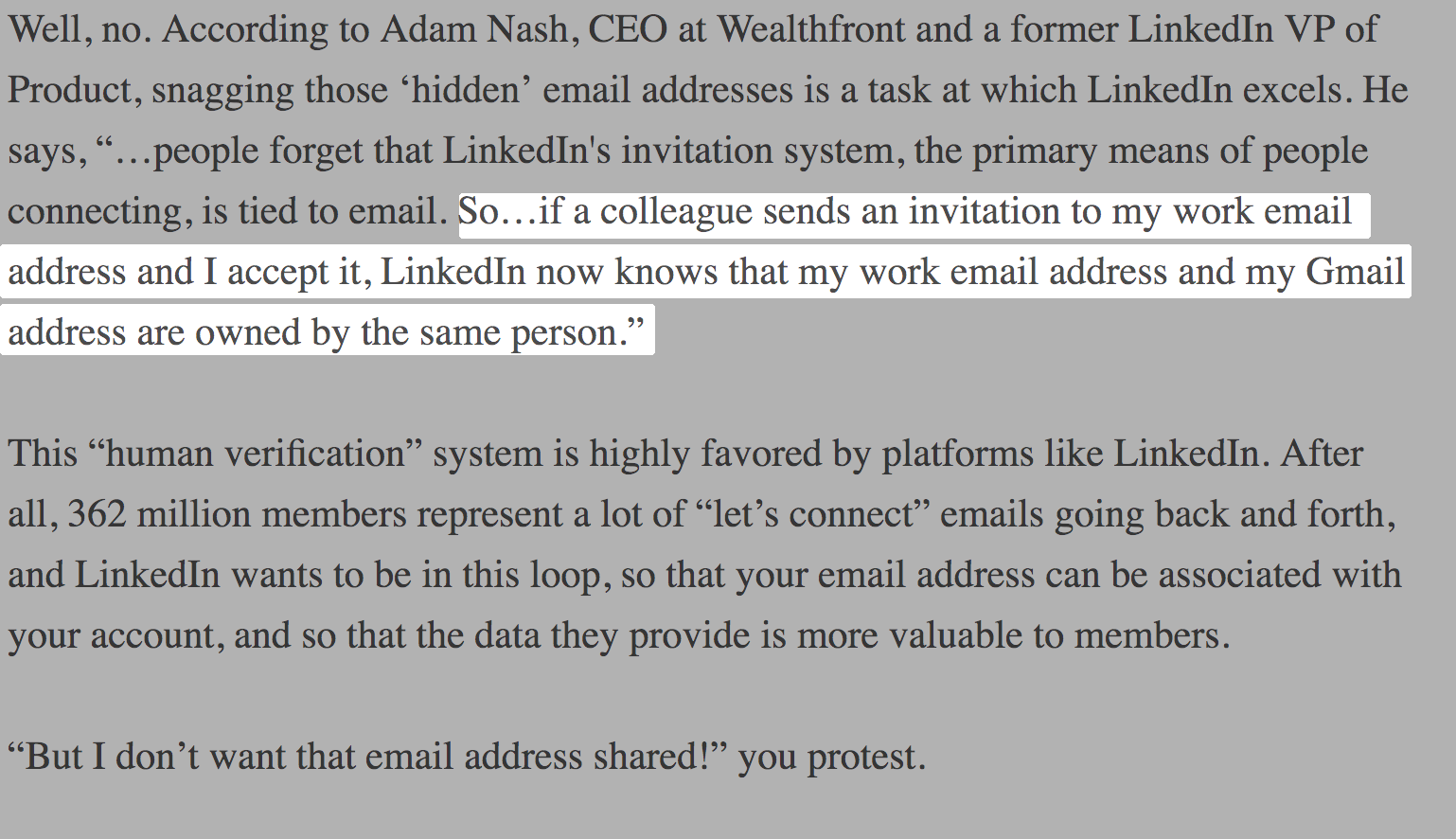
You of course unwillingly gave LinkedIn that information! Remember when you clicked that invitation from LinkedIn inviting you to connect? Well it turns out that once a user receives an invite, lets say at their work email address, and that user has an active LinkedIn session open on their personal account, LinkedIn will assume these two email addresses reference the same person and therefore associate the two emails to the same account.
A former VP of Product at LinkedIn had the following to say regarding 'hidden email addresses':
Ok, so what?
Well it turns out this is a feature, and LinkedIn actually suggests manually adding a secondary email for the purpose of account recovery (if you lose access to one of your emails for whatever reason, for example). This also helps inform LinkedIn's contact suggestion algorithm giving you the user a better experience with the platform.
So, why should I care?
Automatic invitations
It is widely known that by allowing LinkedIn to have access to your Gmail account that you are essentially allowing the application to trove through your contact list (frequently emailed or otherwise). What is not so common is the fact that by providing such a level of access, you have granted LinkedIn the rights to invite users to the network on your behalf.
These settings that allow LinkedIn to use your contacts can be reviewed and changed within the mobile application or the website.
So LinkedIn wants me to expand my network and invites colleagues to connect with me on my behalf, so what's the problem? Well, aside from your contacts receiving potentially unsolicited emails either addressed to them specifically, or to a group of which they are a member, this feature paves the way for another avenue of phishing for our adversaries.
Potential phishing scenario
Lets consider the scenario where you or LinkedIn on your behalf invites to its platform an email alias as opposed to your work or secondary email account. What changes beyond the previous scenario?
An alias can have one or more members and is often referred to as an email distribution group. For example [helpdesk, marketting, executive]@example.com
Nothing changes -- in fact LinkedIn will simply assume that email alias is your secondary email. If the user who receives the invitation in their inbox clicks the link from LinkedIn's invitation email, and has an active session LinkedIn session open, that email alias will be associated with that user's account.
The problem with automatic account association with respect to aliased email addresses is that now another member of the group can simply request a password reset via the "forgot password" feature for that aliased email account, and gain direct access to the user's account that had the automatically associated email. This provides attackers with another avenue for account takeover, using LinkedIn's legitimate invitation and account association features.
What should I do about this?
If you thought to yourself when reading this article "hey, I've seen those invitations come through my work email aliases" then it might pay to flag this with your internal IT department. A quick check to understand whether the email aliases, of which you are a member, are publicly available and addressable from outside your organisation. Microsoft Office365 have published guidelines relating to best practices and trade-offs between distribution groups and aliases. These guidelines can also be applied to Google's enterprise suite (GSuite).
Privacy hygiene recommendations
Within the LinkedIn application, have a look under Settings & Privacy -> Login & security and check to see if the email addresses listed here are appropriate for your account. You should see at least one email address here.
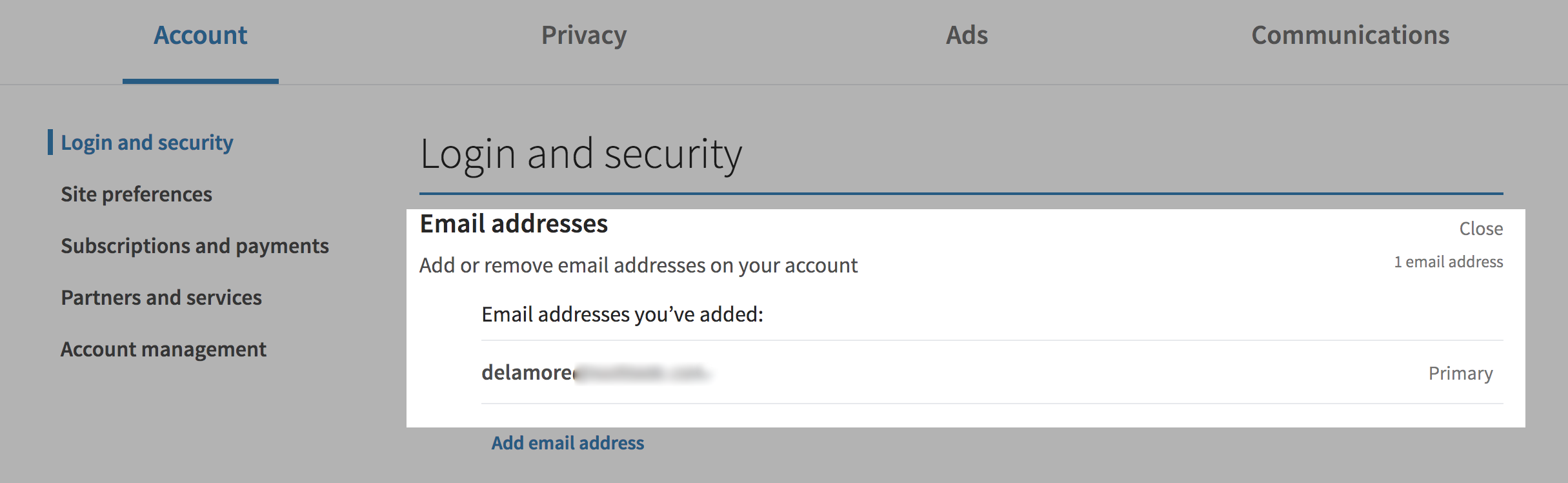
If there are multiple email addresses associated with your account that do not make sense, then remove these right away.
Summary
It goes without saying that LinkedIn is in a league of its own when it comes to providing a platform for networking with like-minded people and connecting you with colleagues both former and present. But in some cases the features and practices that enable its competitive advantage and allow it to be successful can also run orthogonal to our privacy and security expectations. These are trade-offs that we ought not to take lightly, and with GDPR raising the bar for users privacy, incidents like this serve as a reminder that we should be periodically reviewing the amount of information we are sharing with such platforms, and adjusting where necessary.
