Protect Your Online [Brand] At All Costs
![Protect Your Online [Brand] At All Costs](/content/images/size/w2000/2018/07/brand-protection.png)
We've all heard the saying that our brand is our reputation; it is our business card; a prism through which others view us and the way we conduct business. In a perfect world it's a symbol of trust, transparency and security.
If all of this holds true, it therefore follows that we ought to protect our brand at all costs. After all, we are talking about peoples perception of us as a brand and our long-term reputation. As the old saying goes, trust is hard to gain but at the same time easy to lose. Once it's lost, seldom do we get it back. So given how much we care about our brand and reputation we can therefore assume that the cost of protecting our brand should far outweigh negligence, right!? At what cost is the question we should be asking.
In this post we are going to explore the cost/benefit analysis of protecting online brands, and understand what tools and capabilities that can help us achieve the goal of upholding our online brand reputation, without the additional overhead of employing professional services and manual labour intensive tasks.
Lets dive in.
Framing brand in the context of web security
Now this wouldn't be a blog post without me framing this article in the context of security, would it!? So that's exactly our starting point.
Security spend is increasing year-on-year and has been for the past decade. This comes as no surprise to those in industry where tools and services in security take a decent chunk out of our overall budget.
Though with all that said we are still fire-fighting against well known attack vectors such as phishing and brand reputation damage. No firewall, signature or heuristic based intrusion detection/prevention system is going to mitigate this. (Yes, I'm looking at you Baracuda!)
From a defensive standpoint it is easy for our knee-jerk reaction to be:
- block the sender
- block the attachment type
- block the embedded link
- send an email out to our colleagues informing them to be on the lookout for such things
While the above steps are necessary in mitigating the problem adhoc, they are not sustainable long term with respect to targeted attacks simply because at each step, all of the things that we are concerned with flagging are constantly changing. This is the definition of polymorphism (the ability to change dynamically without human intervention).
Where should our efforts be focused?
Spam comes and goes and we need only take a look at our Junk and Inbox folder to understand this is an ever-growing problem. Service providers like Microsoft and Google do a fantastic job at scrubbing most of this -- but not all. Hence why these emails are still visible day to day.
Our efforts should be focused on those targetted attacks. What I'm talking about here is effort undertaken to register a domain (similar to one that we own), and the pretext for these payloads. Pretext in this sense is context around what you would expect to see from a sender. Examples that come to mind are:
- notifications for common services that we use
- tracking websites for parcels
- services that are directly related to our job function
- call to action on some urgent issue about which the sender knows the context
The above "call to action" could be payment information, shipping details confirming your address or parcel pickup, or simply a business related discussion to which you are expecting a response.
The evolution of impersonation and reputational damage
Both spam campaigns and brand impersonation have evolved to the point where users have become immune to clicking links from untrusted senders -- for the most part, and visiting sites which are considered untrustworthy. With the inception of HTTPS becoming mainstream we are now seeing browsers notify users of an insecure page when when visiting sites without a valid certificate. Adversaries are now paying attention to this and following suit with their campaigns to give the perception of trust.
Note: HTTPS has nothing to do with a site being "secure" or "trustworthy", it's an assurance that your traffic, to and from the website, has not been tampered with or eavesdropped during your browser session.
So, why should I care?
If you're in the business of domain protection and reputation, these new attack vectors should be taken seriously. When someone wants information from you -- either financial data, intellectual property or otherwise, they will go to whatever measures required to obtain the perception of legitimacy. This includes registration of domain names, acquisition of SSL certificates, and more.
Just imagine how many of your user and customer base accidently types the wrong domain name into their mobile device or laptop. Not many, true. But the value lost in that user doing so is easily quantifiable if the metrics are available -- we know this simply because there's value in adversaries registering domains that are similar in name to ours. They wouldn't be doing this if it did not yield a return. It's simply cost versus yield, and it works.
Certificate transparency
We've talked about reputational damage with respect to our brand, particularly around permutations or variations of our brand name. But what about our brand, our legitimate domain name? Can this be compromised, even with a validate SSL certificate which we've paid for?
The answer is yes. And these are not one-offs as we like to say [1, 2, 3]. These links are just a small subset of articles related to rogue certificates being issued that are used for nefarious purposes. The references include Google, Microsoft and others -- we could go on. The crux of this is that CA's do in fact make legitimate mistakes and can, and often do go rogue from time to time. The consequence of this is that your traffic, to and from these services, can be intercepted and read by a malicious party. This includes usernames, passwords, emails, conversations and any other information shared with such parties.
A solution to the problem is Certificate Transparency (CT) which aims to address the rogue CA problem, and empower the user to gain visibility into changes made to their domain.
CT next steps
So when do us as users get to take advantage of this new CT verification method? Great news! Google Chrome will be building this into future Chrome browser iterations. What this essentially means is that all SSL certificates issued in ones name (like your personal site, or business domain) will have to be registered in one of the many public ct logs available, thereby allowing your certificates to be auditable by anyone, anytime. And those SSL certificates not registered will be revoked by major browsers (you've seen the certificates warnings before, right?)

The upside to this approach is that us as users will get to see what certificates have been issued by CA's to our domains, thereby giving business' the opportunity to understand the scope of the issued certificates, and identify certificates issued by rogue certificate authorities (e.g., malicious users who are impersonating our brand, purporting to be our domain). All of this will be in the public domain which is fantastic news for those in the security, privacy and transparency space.
The downside to this is that, well, you're going to have to manually parse these certificates and decipher for yourself which are malicious, and which are benign. Following this, it is your responsibility to follow up with the CA to contest such an issue. Moreover, a standard reporting mechanism for such things has been hard to come by. Some exist, but require extensive registration processes, or paid professional services that limit you to the number of domains observed. Many of these services fail to provide a simple lookup for domains that business' care about.
What can I do about this?
To summarise, we've covered both brand reputation damage (malicious users registering domains that are similar to ours for the purpose of phishing campaigns, or simply harvesting our traffic based on a typo/misspelling), and certificate transparency. (the ability to see what certificates have been issued in our name, and others)
Both of which fall under the umbrella of malicious activity and can hit us where it hurts. This includes both loss of revenue due to end-user mistakes with typing domain names incorrectly, and resources spent identifying, blocking and eradicating malicious email campaigns purporting to be our business domain.
A free service that addresses both brand impersonation and rogue certificates
There exists a free tool out there that allows you to see who has registered a domain that is a permutation or variation of spelling to your domain, and gives you a crystal ball preview into what that website looks like in semi real-time, without you even needing to visit the site! Imagine, you can see who is impersonating your domain, which domains (or permutations of) belong to you, and which permutations are yet to be registered.
All that is required from the user is the domain name they want to analyse. What's cool about this is that you don't need to worry about spam, malware or the potential of getting phished on your end; the service visits these sites and produces a screenshot of it so you don't have to. Here's a preview:
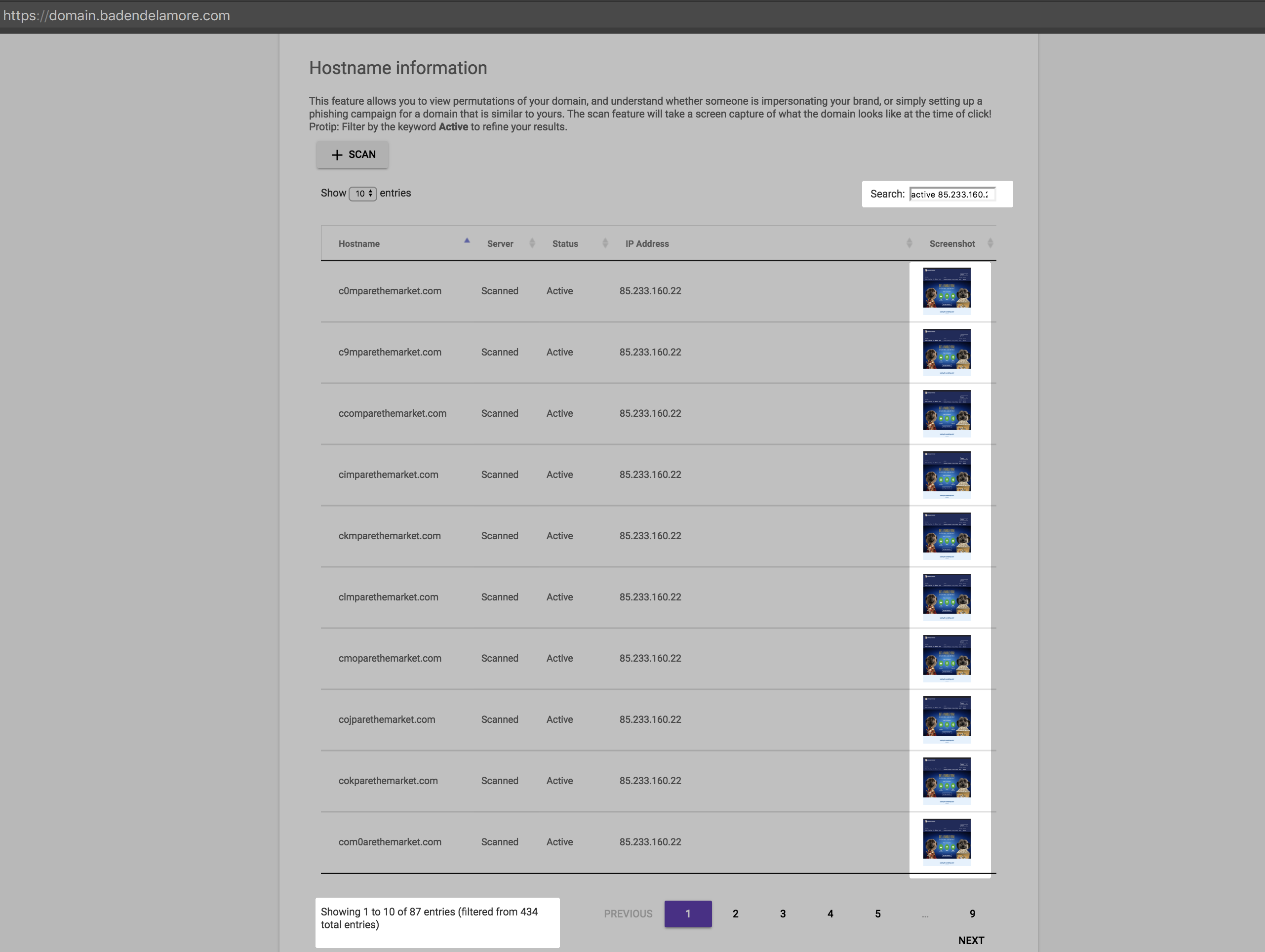
The portal provides you a simple table-like structure that allows filtering. Some useful filters include:
- "Active": This filters all domain permutations that are currently registered
- "Unregistered": This gives you a list of unregistered domains (do it, now!)
- Scan functionality: This allows you to see what is hosted on that domain (use this in conjunction with the "Active" filter)
- "Table results": Allows you to see x number of results at a time
One key thing you can do with this is filter by IP address too. This allows you to understand the percentage of domains that belong to you, versus the number of permutations actively available. The beauty of this tool is that you never need to visit these sites yourself, instead let the tool do the work for you, and sit back and see if there are people registering domains similar to yours for the purpose of clicks leading to revenue, or potential phishing websites (e.g., sites that look like yours, but are not). If this is the case, you are now equipped with the information necessary to take action.
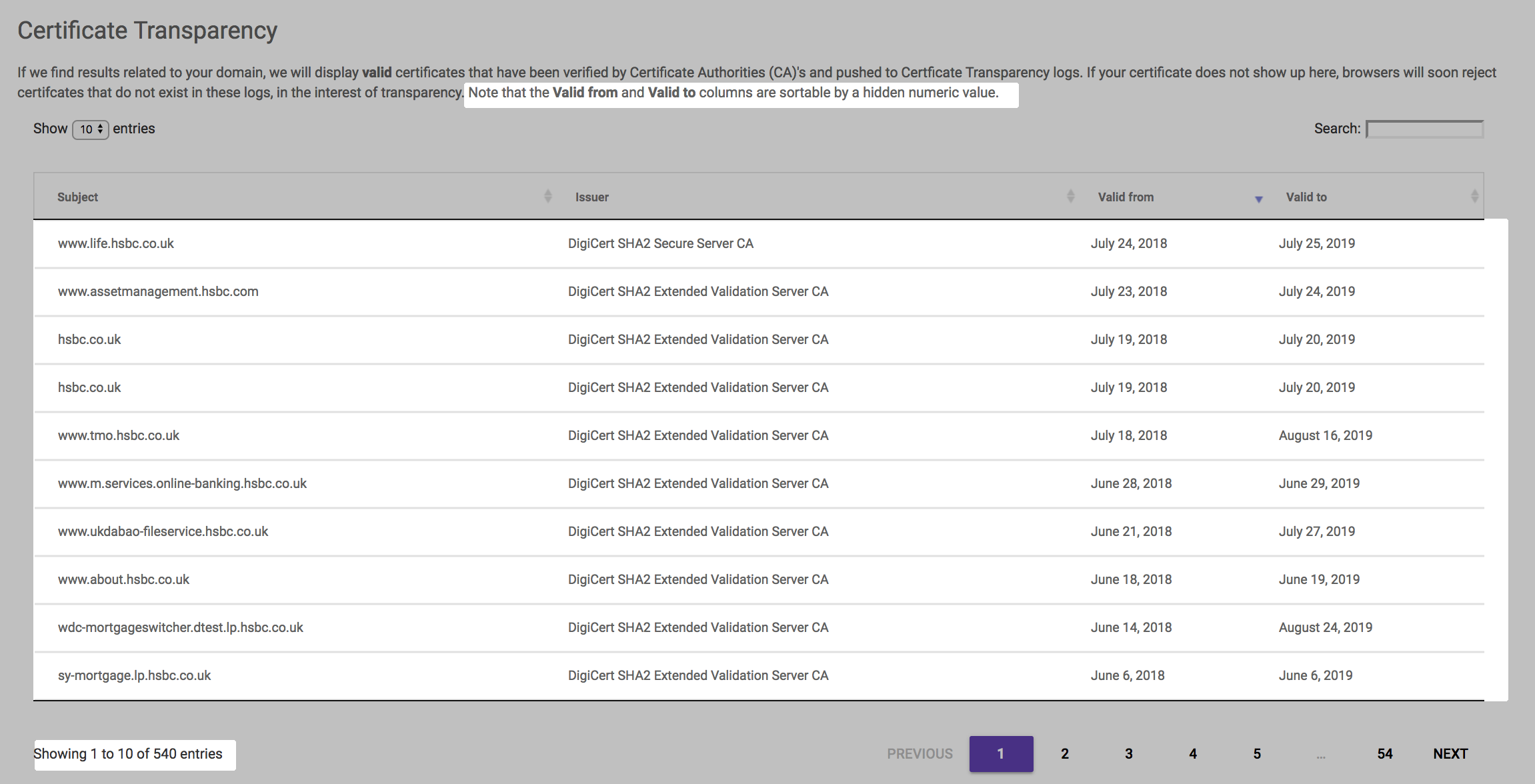
Certificate transparency
Hop over to the next tab and you'll see all the valid SSL certificates registered in your name. This feature allows you to sort by registration date to understand what are the latest certificates belonging to your domain, and gives you an understanding of who registered what/when and through which CA. This information is updated every day so you'll be getting the latest and greatest from this API endpoint. If you don't recognise a particular CA, then it's time to file a complaint with that CA -- this is indicative of rogue CA's issuing certificates on your behalf, without your knowledge.
Subscribe to changes
The service also allows you to subscribe to events that includes both certificate transparency changes (e.g., new certificates issued belonging to your domain), and any changes to domain permutations. This will give you an insight into whether someone has registered a new domain permutation similar to yours, or any other changes relating to your domain. This includes Mail Server (MX) records, Name Server (NS) records, and Alias (A) records. This might sound a bit techy, but this information is vital in understanding your potential attack surface.
The subscription feature is in preview and will be changing regularly over the next couple of weeks
Free of charge
All of this information, including the domain name permutations, CT data and subscription service is provided to you free of charge regardless of how many domains you wish to monitor, including the ability to see what other domain names are available and registered or those domains unregistered (go, do it now!). Moreover the subscription service allows you to be alerted any time changes are made either to any of your domain name permutations or CT log information.
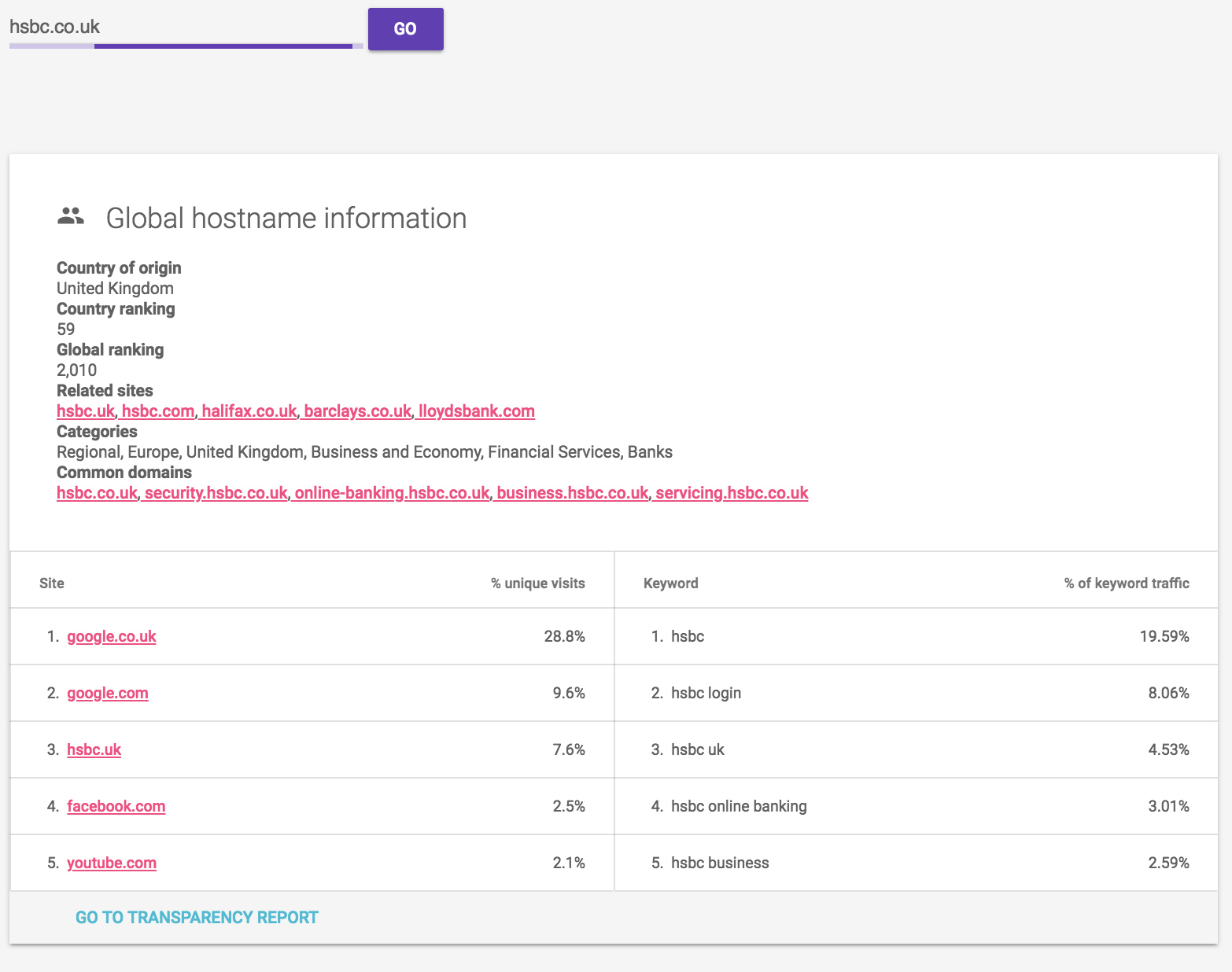
Global ranking preview
We'll also give you a quick snapshot of metrics associated with your domain where possible. This includes ranking -- both local and global, and includes keywords associated with your domain and sites that are upstream to yours.
Where can I find this?
So I built this tool in my spare time. It's freely available, and always will be at https://domain.badendelamore.com
How did you build this?
The technologies used for this tool are:
Javascript NodeJS- server-side using asynchronous patternsJavascript/MDL- client-side rendering and layoutMongoDB Cloud- persistent NoSQL document db data storageDocker- containerizationGit- version controlCloudflare- Web Application Firewall (WAF) with API rate-limiting
I'm open to collaboration so feel free to flick me an email or LinkedIn message with your thoughts, or alternatively a chat over a cup of coffee or beer works just as well.
Summary
The cost of registering the permutations of your business domain is a drop-in-the-bucket compared to the effort required to monitor such domains. For 100 domains, you're looking at around $700-800 per annum. Compare that against the amount of time/effort required in fire-fighting scammers who are registering these permutations hoping they'll receive some of your traffic over time, or coaxing your users to click a link that appears to be like your domain. Moreover, you can rest assured that potential phishing campaigns wont arise from misspellings of your domain, because you registered them first. These facts do not even quantify the time taken investigating, blocking, and eradicating such campaigns which can easily run into the tens or hundreds of thousands per year. My suggestion? Use this tool to your advantage, and free up your resources to focus on what really matters. Like building new tools :-)
Enjoy!
